Clear Concepts Insights
Stay connected with our IT experts. Clear Concepts Insights is our vehicle to share information and opinions that matter.
Latest Posts
The AI Imperative - This Hits Home
Microsoft and LinkedIn have just released their annual Work Trend Index (WTI) Report. It should come as no surprise that the WTI documentation this year is packed with information..
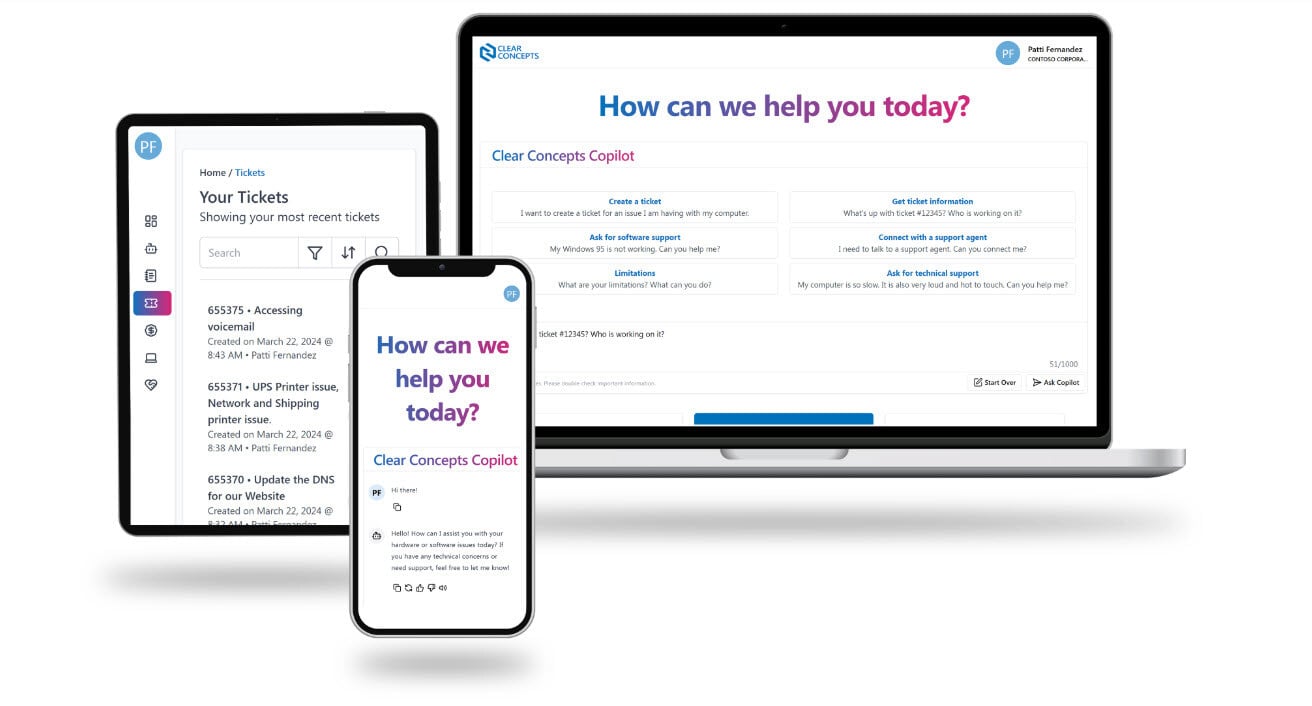
Getting To Know Microsoft Copilot
Microsoft Copilot is a powerful tool that can help you boost your productivity. Whether you are writing reports, proposals, presentations, or emails, Microsoft Copilot can assist..
Innovate For Impact
On December 6th, 2023, Clear Concepts hosted a group of local non-profit organizations at our inaugural, Innovate for Impact session. This unique event was a first for Winnipeg,..
How To Get Started With AI: Productivity
Generative AI is a rapidly evolving technology that promises to transform many industries and sectors. However, we are hearing from small businesses that the idea of adopting..
Empowering Inclusion: Highlights from Microsoft Ability Summit 2023
The Microsoft Ability Summit is an annual event dedicated to empowering individuals with disabilities. The summit brought together diverse voices, cutting-edge technology, and..
Creating Private Planner Boards with Microsoft Loop
Planner may not have changed much since my last rant blog post back in 2022. Since then, the product team has added a few features from the backlog , including re peating tasks,..
Exploring Use Cases for SharePoint Team Sites [Office Hours June 2023]
Earlier this May, Microsoft announced the future of SharePoint with the world. This inspired us to focus this month's Office Hours on SharePoint sites, looking at different way to..
The Risks of Bulk Emailing Through Microsoft 365
As businesses and organizations continue to rely on email as a primary means of communication, the need to send bulk emails has become increasingly common. However, sending bulk..
Use Cases for Channels in Microsoft Teams [Office Hours May 2023]
Are you curious about how to get more out of Microsoft Teams for your department, committee or entire organization?





.jpg)


