Email Threats: Homograph Exploits and Extortion Scam

Regular SPAM filtering just isn’t as effective as it used to be. We live in a time where threats are evolving on a global scale, rapidly working to disarm even the best email filtering solutions. Time and time again, new exploits of Phishing and Spoofing are designed to take advantage of the human condition. Here are two of the more advanced tactics currently being utilized to gain access to private data or extort money:
Homograph Exploit
Homographs are usually a pair of words that are spelled the same way but sound differently when pronounced. For example a Bass the fish or Bass as in sound or instrument. A Homograph Phishing Exploit is based on the attacker registering a domain name that looks like an official domain name, commonly attempting to impersonate being from within the same company or from an official government agency, like Revenue / Taxation or Law Enforcement. The similarities usually involve the substitution of letters like interchanging lower case i for lower case l or use international characters that have similarities to English.
Here are two examples:
The first one takes advantage of international characters - Apple is the one of the most well known brands in the world but visit https://www.apple.com/ and then https://www.аррӏе.com/ (links are safe to click). Obviously they look identical but the second one uses an international Cyrillic (a.k.a. Greek) letter A instead of the standard ASCII one.
For the second example, look at the following two email addresses: john.doe@smlthvillepolice.ca versus john.doe@smithvillepolice.ca. At first glance it is extremely hard to tell the difference and most SPAM filters will let these pass through as there is no need to cover-up the sending address with a fake Display Name. The Display Name of a senders email address can very easily be manipulated and many SPAM filter rules can block this approach, so Homographs are becoming more popular. Once the hacker builds trust that the email is from users own company, or from a government official, it is relatively easy to complete the exploit by linking them to a realistic looking website to capture Social Insurance Numbers, Banking Information, Credit Card Numbers, or other personal details. The Homograph exploit is very difficult to protect against so be extremely cautious when receiving an unexpected or unusual email request.

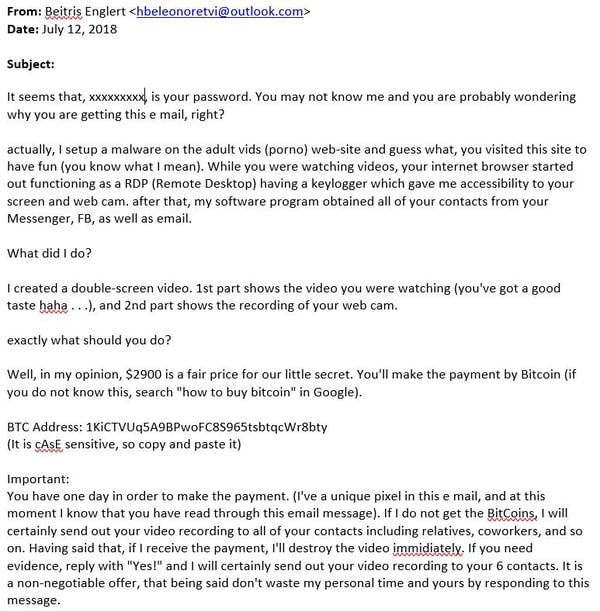
Extortion Scam
The second tactic that is commonly found right now is the Extortion Scam. This exploit is on the rise because it successfully creates fear that hackers possibly have your passwords and video recordings from your webcam - unless the recipient pays a sum of money via Bitcoin ($300 to $3000), they will send the video recordings to friends, family, and co-workers. The hacker builds credibility by including one password that the target has used in the past. Email and password combinations from previous hacks and corporate data breaches are available for sale on the dark webs so any scammer can buy these low cost lists and utilize the combination to send thousands of emails. If only a handful are successful they have made a sizable profit. If you are still using the password the email refers to, change it immediately. If you want to check if your email address has been compromised in a past data breach, use this site to find out: https://haveibeenpwned.com/. This is a very common scam but easy to fall into the trap because of the use of a personal password. Do not pay the Bitcoin ransom as they most definitely do not have any video from your computer.
Here is how to protect against being exploited by these tactics (and similar):
- Official notifications from government agencies like Law Enforcement or Taxation do not get sent via email so you should immediately be suspicious. Make a phone call to verify if you think there is some legitimacy to the request.
- Carefully review the email sender information, including the email address and display name. If they don’t match, or there are other irregularities such as being sent from international email accounts, this is a sign the email is a scam.
- Unless you have specifically requested it, any email asking for a password reset verification of account information should be closely reviewed.
- If you receive an unusual, out of character request via email from a co-worker, call them to verify before replying or clicking any attachment or web link.
- Reset passwords on a regular basis or use a password manager.
- Utilize 2 Factor Authentication (2FA) as a second level of login protection - many online services have 2FA available, find out here: https://twofactorauth.org/
- Consider adding more advanced email protection on top of your SPAM filter.
In order to help protect again these and many other email exploits, we are recommending more intensive SPAM and Threat Protection be enabled to scan incoming email. If you are already on Mirosoft 365, Microsoft offers a perfect add-on solution called Advanced Threat Protection or ATP. This low-cost upgrade adds the following layers of protection:
ATP Safe Links proactively protects you from malicious web-links (hyperlinks) in a message. The protection remains every time they click the link, as malicious links are dynamically blocked while good links can be accessed.
ATP Safe Attachments protects against unknown malware and viruses, and provides zero-day protection to safeguard your email. All messages and attachments that don't have a known virus/malware signature are routed to a special environment where ATP uses a variety of machine learning and analysis techniques to detect malicious intent.
ATP Spoof Intelligence detects when a sender appears to be sending fake mail on behalf of one or more user accounts within one of your organization's domains.
ATP also includes Advanced Anti-Phishing capabilities which use machine learning models to detect phishing messages.
Concerned about homograph exploits and extortion scams? Reach out to us today for expert guidance. Don't wait for threats to escalate – let's fortify your digital defenses together.
